Sometimes software vendors will announce a vulnerability in their software, even before they have a patch available to solve the issue. They will often provide some information publicly which can be enough to help users avoid the problem, at least partially.
Application Control, available in some of our Business Security products, can in some cases be used to quickly help protect from the vulnerability.
As an example, Microsoft announced on March 23rd 2020 a vulnerability in their font parsing. More details can be found at https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/adv200006
Included in their advisory were some details of mitigation steps users can take. One of these was to prevent the loading of an operating system binary, ATMFD.DLL. Their recommendation was to rename the binary, and to do this administrator rights are needed on each computer.
With Application Control, it is possible for the organization’s administrator to create a rule to prevent this binary being loaded, and to share that rule to all of their computers, automatically helping to mitigate the problem.
To create the rule, the admin needs to make a few small modifications to the “profile” used by the F-Secure software. In the following example, we will use Protection Service for Business, but similar actions can be made with our Business Suite software.
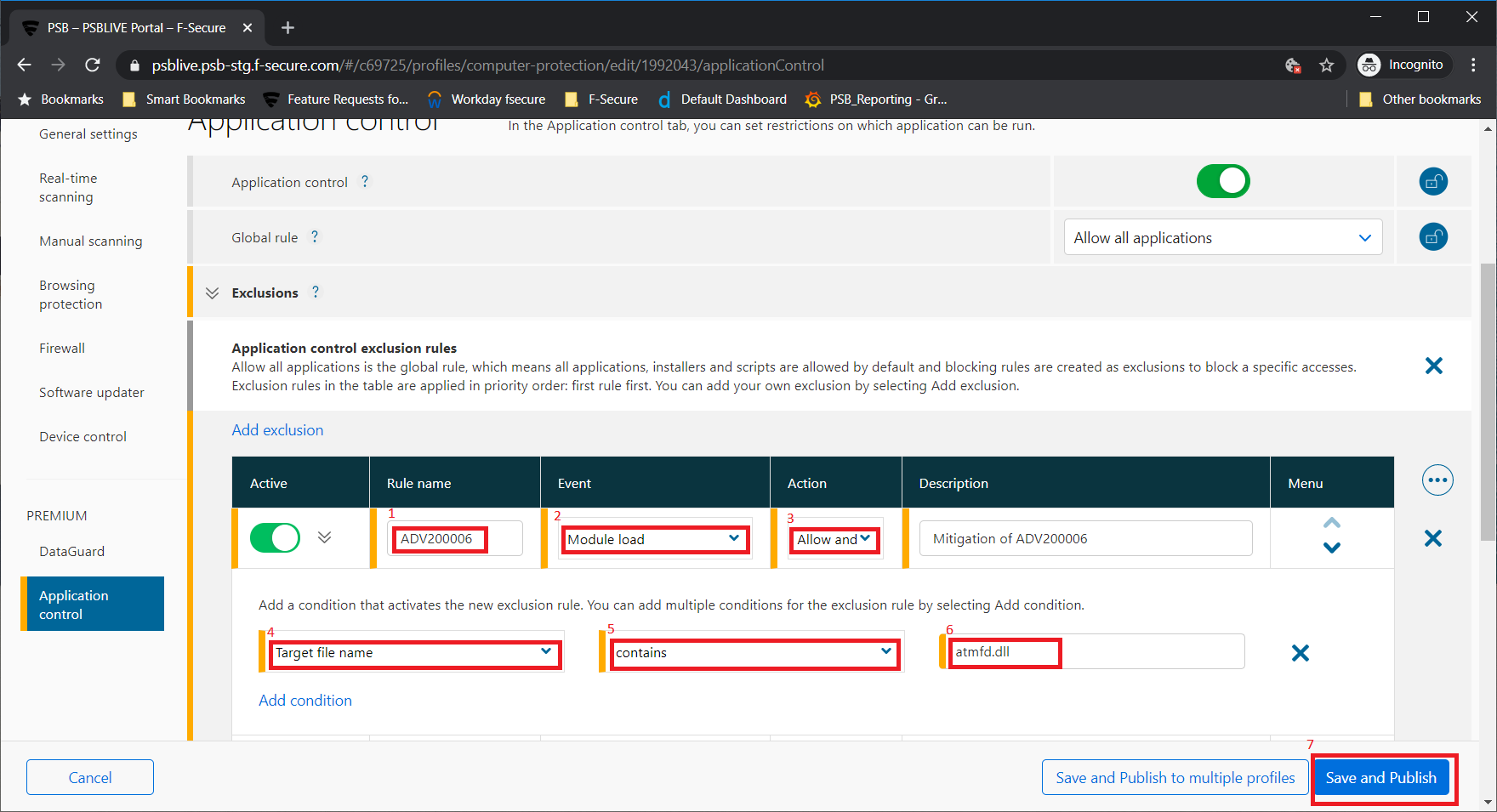
- Select the profile in the PSB portal to edit.
- Choose “Application Control” on the left side menu
- Add an exclusion
- Rule name (1) – this is freeform text, but we advise naming it so it relates to the particular advisory, so when you come to review rules it is quite obvious what it is for.
- Event (2) – Choose “Module load”, as this is a DLL (library module) that we want to work with
- Action (3) – Initially, choose “Allow and monitor”, as this will report to the portal if something tries to load the module, but will not block the action. Very handy for testing rules!
- On the second row of the rule creation, select an attribute (4) from the drop down menu. In this case we want to select “Target file name”.
- Select a condition (5). In this case, we want to select “contains”
- In the final box (6) on the second row, enter atmfd.dll
- When all the fields have been set, “Save and Publish” (7). This rule is then sent to all computers that are using this profile.
After this, any computer attempting to load this module will report to the portal. When the administrator is happy the rule is detecting correctly, and not interfering with business critical applications, they can edit the rule so that the action becomes “Block”.