We are thrilled to announce that our Automated Actions feature has been extended to support running response jobs for Identity Security for Entra ID BCDs (Broad Context Detections). This enhancement is designed to provide more robust and efficient identity security management, particularly for cloud environments, ensuring that your systems are protected with minimal manual intervention.
New Capabilities:
- Customizable Response Actions: You can now select from three specific response jobs—End Current Session, Reset Password, and Block User Access—to run for BCD risks starting from Medium and above.
- Exclusion Options: We have introduced the ability to exclude certain identities from running these jobs, providing more control and flexibility in managing your security protocols.
- Custom Scheduling: Automated actions can now be scheduled to run outside business hours if desired, offering flexibility to minimize disruption to daily operations.
Note: In the customer’s Azure tenant, the WithSecure Enterprise Application for Identity Response utilizes the User Admin role to adhere to the principle of least privilege and minimize risk. This imposes limitations on performing WithSecure Identity Response actions against the primarily privileged roles, see the guide.
How to Set Up Automated Actions:
- Add Rule: Navigate to Automated Actions and click on "Add Rule".
- Give a Name: Enter a name for your rule.
- Select Rule Type: Choose "Identity and Cloud" as the rule type.
- Select the Response: Choose the response actions you want to implement.
- Target Organization: Select the organization you want to target with two options:
- Multi-Organization: Limits the scope to all identities.
- One Organization: Extends the scope so you can exclude some of the principals.
- Choose Risk Level: Select the risk level or any combination from the following:
- Medium
- High
- Severe
- Select Schedule: Choose between Continuous or Custom scheduling.
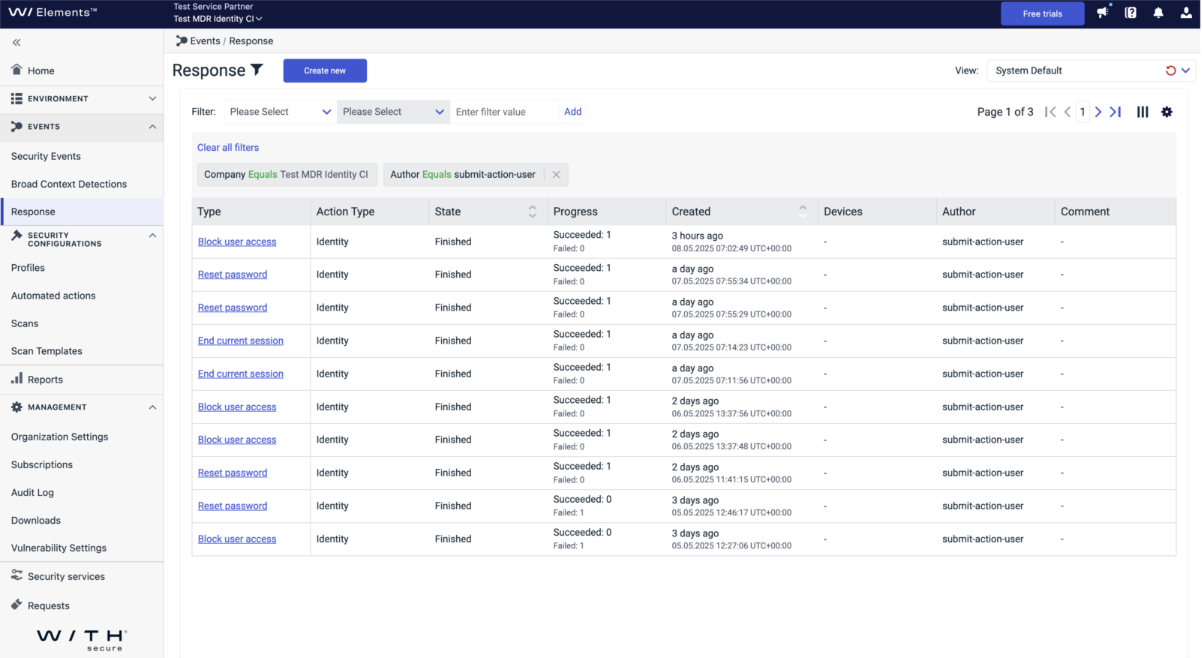
Once a rule is matched, the response run will be logged in the Response section.
With these new capabilities, you can now automate critical identity security tasks, reducing the risk of security breaches and enhancing overall system integrity, especially within cloud environments. Stay tuned for more updates as we continue to improve and expand our security solutions.
Full Setup Workflow for Automated Actions in Identity Security
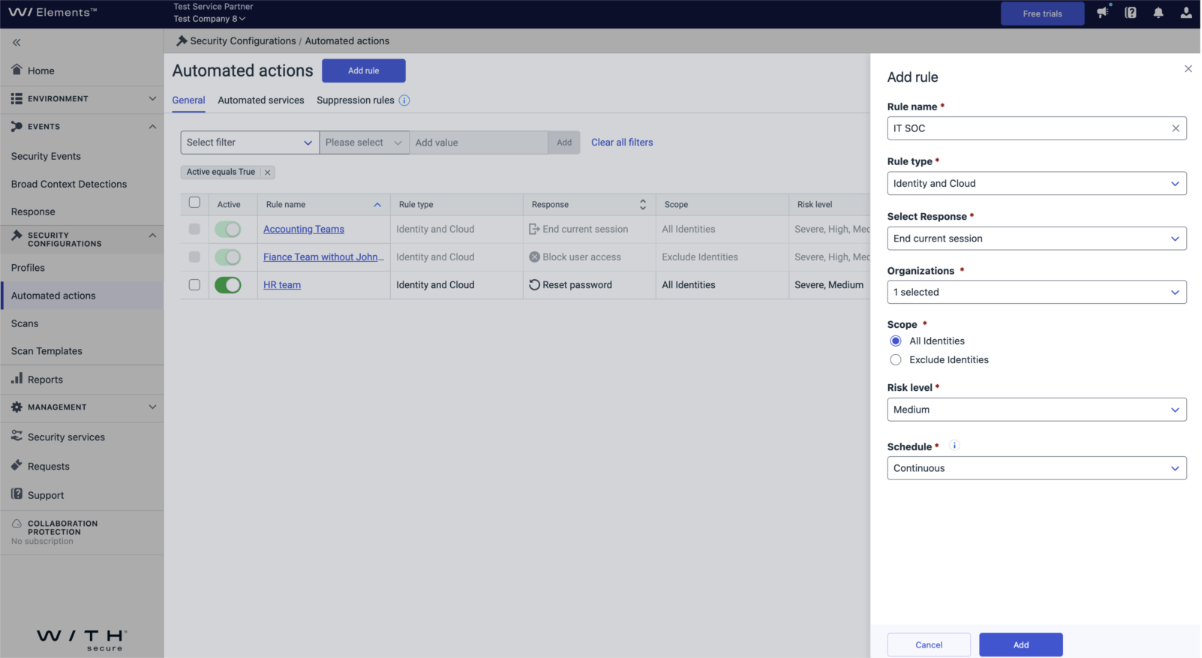
Outcome – Rule Creation Interface
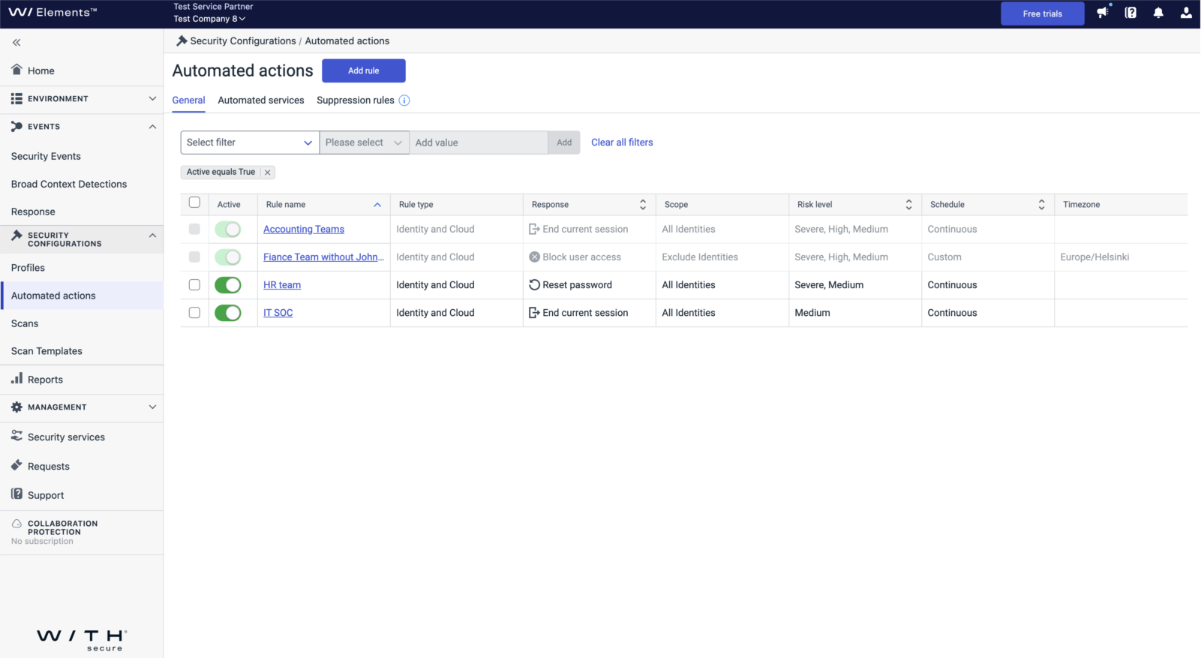
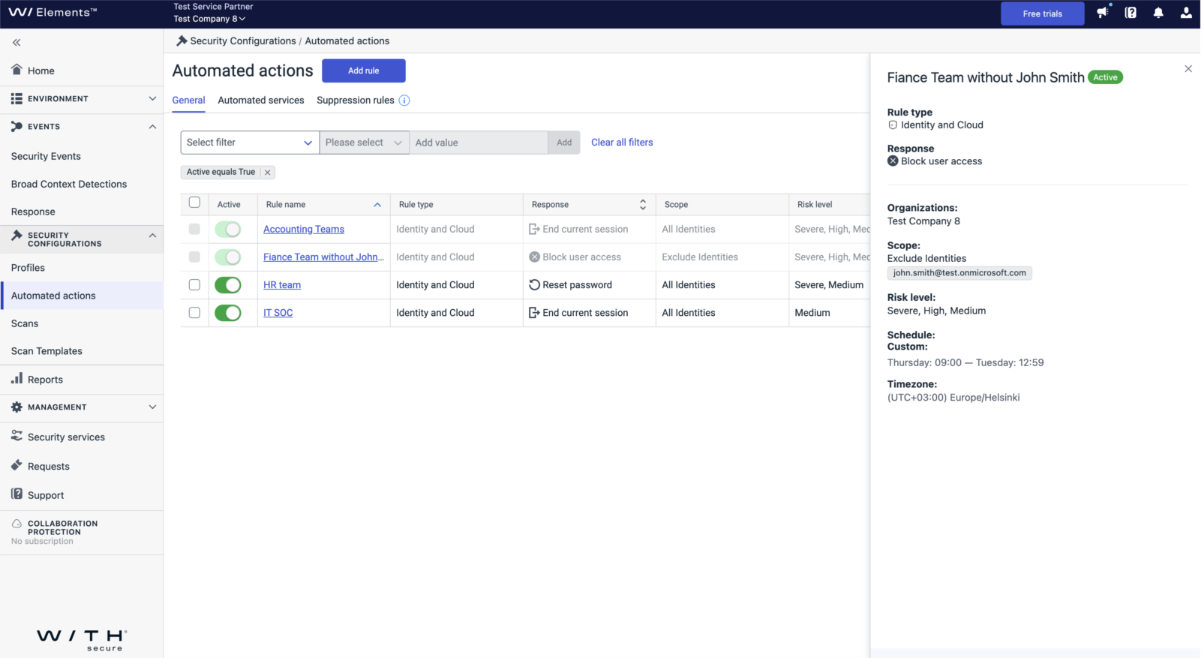
Outcome – Response Job Execution Log