Editor’s Highlights
Breaking News
Even though this article relates to releases in April, we want to announce that Software Updater for Mac is now available. Please see
https://community.withsecure.com/en/kb/articles/29796-software-updater-for-mac
for more information. Fuller details will be included in the May What’s New article.
Elements Security Center
It is now possible to manage devices that have been removed
Administrators can use this feature to restore individual devices that have accidentally been removed or blocked. This feature will replace the existing "Restore devices from blocklist". This feature is placed under three-dot menu in device list view.

Software Updater summaries have more information and improved filtering
- Help text has been added for Bulletin ID columns
- The Bulletin ID column has been added to Installation Logs tab
- It is now possible to filter all devices that have installed some patch using Bulletin ID filter on Installation Logs tab.

Quick Filters are now available for selected columns in the Security Events table.

Profile editor changes
- We have added a new section called "All settings". This section contains all possible profile settings in one view.
- There is now a search box on top of every section which allows to free form search for settings or their values.

New unprotected devices features
- The administrator can now enable automatic daily scanning for a company.
- Devices found by the scan now can be marked as trusted and it is also possible to add comments for the devices found by the scan.
- It is now possible to filter the list of unprotected devices by Active Directory Group and trusted status.
Device listing changes
- A new column was added to the device listing, called "On public internet". This describes whether any of IPv4 addresses of the device are public.

Security Events changes
Additional Quick Filters are now available in the expandable section:

- Filtering by device label

In the Security Events section we have introduced a feedback form to
encourage customers sharing their feedback about recent additions and
ideas for future features.
Elements Endpoint Protection
WithSecure Elements Agent for Windows and Server version 23.3
A new version of the endpoint clients is available.
This release makes the Elements Agent version 23.3 available (internal version 23.3.570), and the endpoints automatically upgrade, without a reboot.
Authenticode signing changes
This release is signed with a new WithSecure Authenticode certificate. Our very old installers don’t know this signature and will not trust it. If you use very old network installer - please upgrade to latest otherwise your installations will fail.

Automatically discovered network shares are displayed in the portal

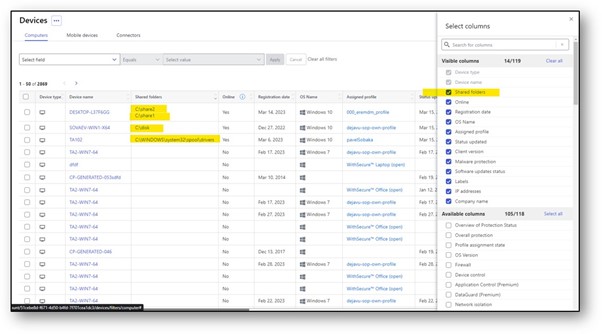

The Devices view now shows the UUID type the device was installed with (unique, smbios or adguid)

Multiple proxies support
Profiles now support specifying multiple proxies and Connectors separated by semicolon. Please note that clients prior to 23.3 don’t support multiple proxies and may break so it’s advised to use it only with new clients or wait for all devices to upgrade to 23.3 first.


Delay automatic USB scan
When inserting a USB device, the automatic scan is now delayed for 5 seconds to give device control time to disable the device if needed.
Connectivity report in fsdiag
This release checks accessibility of 2 new URLs:
These URLs will be taken into use in a future version of the Elements Agent so please verify they are not reported as not accessible for your devices.
Elements Vulnerability Management
Added support for ed25519 and SHA2 keys in scan templates and configurations
RSA-SHA1 keys are deprecated by OpenSSH and no longer supported on newer systems like Ubuntu 22.04 LTS. By adding additional key exchange algorithms, we ensure scanning can continue uninterrupted.
Enhanced vulnerability instance detail view
We have now added a 'First seen' date, which indicates the date when the vulnerability instance was initially discovered. Also added a 'Last seen' date to the vulnerability instance detail view, which reflects the most recent occurrence of the vulnerability instance in an incoming report.

Elements Vulnerability Management System Scan
We have now added multiple detection capabilities to the System Scan:
- Detect vulnerabilities in NXLog Community Edition in authenticated scanning for Windows
- Detect vulnerabilities in 3CX Desktop App in authenticated scanning for Windows including CVE-2023-29059 vulnerability (about trojanized versions of the software).
- Detect vulnerabilities in PostgreSQL JDBC Driver in authenticated scanning for Windows and Linux
- Detect vulnerabilities in Wondershare MobileTrans in authenticated scanning for Windows
- Detect vulnerabilities in Wondershare Filmora in authenticated scanning for Windows
- Detect vulnerabilities in Wondershare PDFelement in authenticated scanning for Windows
- Detect vulnerabilities in Wondershare Repairit in authenticated scanning for Windows
- Detect vulnerabilities in Wondershare Creative Center in authenticated scanning for Windows
- Detect vulnerabilities in Wondershare PDF Reader in authenticated scanning for Windows
- Detect vulnerabilities in Wondershare Edrawmax in authenticated scanning for Windows
- Detect vulnerabilities in Wondershare Recoverit in authenticated scanning for Windows
- Detect vulnerabilities in Wondershare Anireel in authenticated scanning for Windows
- Detect vulnerabilities in Wondershare DemoCreator in authenticated scanning for Windows
Integrations
Reminder: Legacy APIs will stop working soon
We are progressively deprecating the Endpoint Protection API and replacing it by Elements API.
The following endpoint will reach their end of life soon:
- Computers endpoint: 30th of May 2023 (see change log)
- Security events endpoint: 30th of June 2023 (see change log)
- Companies endpoint: 31st of July 2023 (see change log)
- Invitations endpoint: 3rd of November 2023 (see change log)
Elements API: Managing EPP invitations
An authorized client can manage EPP invitations:
The Legacy EPP API for managing invitations is deprecated.
Other items of interest
Monthly Threat Highlights Report: March 2023
Ransomware: Trends and notable reports
- CISAs pre-ransomware notification initiative
- Dole attack shows real world impact
- Rise of Royal
- Nevada is Nokoyawa
- Magniber’s SmartScreen bypass
- Ransomware newcomers
Other notable highlights in brief
- Best practices in cyber
- Hydrochasma gathering intelligence
- I2PMiner targeting MacOS
- Lumma Stealer targets content creators
- T-Mobile constantly targeted by SIM-swappers
- Android banking trojan tracker
- Breach Forums down!
- Ultrasonic attacks
You can also Download report
In case you missed it
Share your ideas with us
Our purpose is to co-secure the world with you – now as WithSecure™. To co-create the best possible cyber security products and services, we warmly recommend you share your ideas via our Ideas Portal, now accessible directly from WithSecure™ Elements Security Center.

Further information
Changelogs and Release Notes for all parts of WithSecure™ Elements can be found at the Help Center