Introduction
We are preparing the End of Life (EOL) of WithSecure Elements Vulnerability Management (EVM), where EVM is replaced with the more comprehensive and intelligent solution - WithSecure Elements Exposure Management (XM).
XM includes and is not limited to
- From reactive and asset centric to proactive and estate-wide security.
- Gain visibility on what attackers would be able to do in your estate.
- Easier and more efficient prioritization of work.
- AI assistance for remediating and documenting your exposure.
- Expand your visibility beyond devices. E.g. EntraID, Azure and AWS.
We are now highlighting a few fundamental changes that will impact EVM, and also when you continue using similar features in XM product.
EVM Ticketing User Interface
We have decided to discontinue the EVM ticketing system user interface. The earliest date this will occur is 1st December-2025, and by the end of 2025 at latest. The EVM ticketing related user interface can no longer be accessed.
While the ticketing workflow and the related history will continue to be supported via the EVM API, we recommend utilizing statuses of Exposure Management Recommendations and Findings. The recommendations are also accessible via the Elements Security Events API, which can be used to integrate to an external ticketing system. Please reach out to your WithSecure contact to get additional help for the transition.
In case you need to access or modify the EVM ticketing data or configuration via the Elements user interface, we recommend doing it before December 2025.
EVM Vulnerability Users
As previously announced we are changing the way EVM users are managed.
We have decided to migrate Vulnerability Users as part of Elements Role Based Access Control (RBAC). The following user interface is no longer accessible, and the earliest this change will happen will be 1st December 2025:
Management / Organization Settings / Vulnerability Users
The roles and accesses within will continue to function.
While the EVM API can be still used to manage the access, we recommend using the Elements level RBAC found in:
Management / Organization Settings / Security Administrators
This view allows managing user permissions using one of the 3 default roles: Administrator, Team member or Read-only team member. If the user was previously assigned to a custom VM role or roles, it will be represented as a single “Vulnerabilities:Custom” role. VM custom roles can only be revoked using Security Administrators view.
A screenshot below presents the matrix of privileges assigned to the 3 default roles that can be managed via Elements-level Security Administrators page
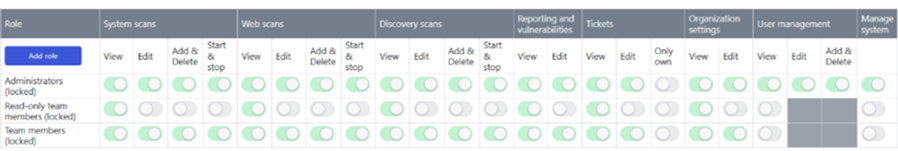
Further changes
We expect changes also to the following areas, as we start using Elements wide solutions.
- Environment / Devices / Device Discovery
- Environment / Devices / Vulnerability assets
- Environment / Exposure / Vulnerabilities
- The functionality is going to be available at Environment / Exposure / Findings
- Further details to come
- Environment / Exposure / Vulnerability coverage
- The functionality is going to be available at Environment / Exposure / Findings definitions
- Further details to come
- Home / Vulnerability Management Dashboard
- The most used widgets are going to be available at Reports / My Report
- Further details to come
- Reports / Vulnerability Reports
- Will be moved under Reports / Email notifications and reports
- Further details to come
The following items will be reimplemented within Elements to become available across the whole of the Elements portfolio:
- Reports / Vulnerability Notifications
- Vulnerability Settings / Notification Settings
- Vulnerability Settings / Event Log
We are currently evaluating how we will present the following capability to the users
- Security configurations / Scans / Network scans