Extended Detection and Response
Endpoint Protection
Elements Agent for Linux Now Available for ARM64 Architecture
We are pleased to announce that Elements Agent for Linux now include support for ARM64-based systems.
Installation packages are available for download in the Download Center and in the Elements Portal.
WithSecure Mobile Protection for IOS
An update to the WithSecure Elements Mobile Protection app for iOS (25.10.11981) has been released
It includes the following fixed issues:
- The app and the WithSecure Elements Endpoint Protection portal now support the SMS Protection setting
- The "Recent Activities" view now shows occurrences for processed and blocked URLs
- Added a filtering option at the top of the list of checked URLs
- Added main screen for iPad devices
- Improvements to app stability
- Fixed an issue where Network Protection could interfere with certain applications' internet connectivity
WithSecure Mobile Protection for Android
An update to the WithSecure Elements Mobile Protection app for Android (25.4.0023361) has been released
It includes improvements to app stability
Exposure Management
We are happy to share many improvements to WithSecure Exposure Management
Recommendation list page (Exposure -> Recommendations)
Recommendation list "Generate on" column is now showing the time of when the recommendation was given in the context of organization. Please note that historical recommendations may show very recent timestamp due to the fact that this info is only available since very recently.
Saved views on Findings, Recommendations and Identities pages
Preserving the state of ordering is now supported by saved views.
Unified Cloud Microsoft tenant configuration
New connection management for Identity Inventory released
Identity details - Risk assessment tab
There is now new possibility to filter Identity breaches by severity
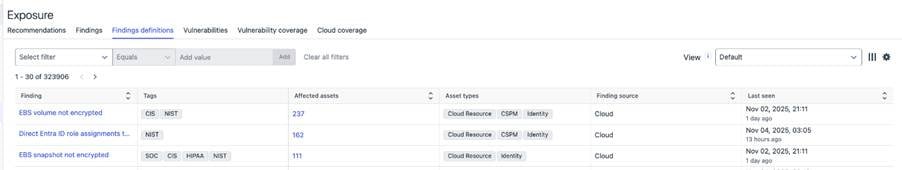
Finding definitions tab added under Environment -> Exposure
The Finding Definitions page now lists all potential finding types that Exposure Management can detect—across vulnerabilities, identities, cloud assets, and external attack surfaces. Unlike the Findings tab, this view includes definitions even if no asset is currently affected. It supports pagination, saved filters, and navigation to related data, consistent with other XM views.
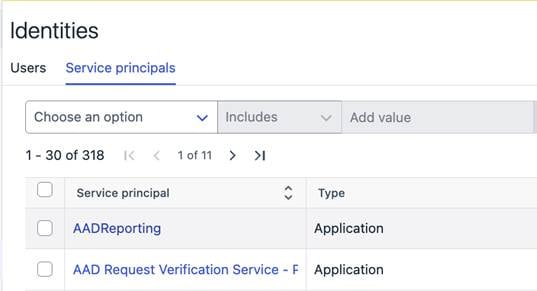
Service principal tab add under Environment -> Identities
The identities list now includes Entra service principals alongside users, providing basic information for each service principal. It supports pagination, saved filters, and navigation to related data, consistent with other XM views.
Exposure Management for Business
New Feature: Identity Inventory
Identity Inventory is a new capability in WithSecure™ Elements that provides a unified place for administrators to configure and manage Entra ID tenants. It simplifies Tenant management by centralizing visibility and control within the Elements Security Center.
You can find out more about Identity Inventory in this dedicated article
Exposure Management Portal
- Improved overall performance.
- Added an info banner to the Vulnerability Users page announcing its upcoming deprecation for all customers.
- Disabled Vulnerability Users page for new Exposure Management customers.
- Added support for logarithmic scales in the VM Histogram widget.
- Resolved an issue that caused errors when opening historical Web Scan reports.
- Resolved an issue where email notifications about low disk space on scan nodes were not being sent.
- Disabled Dashboard page by hiding the tab for new Exposure Management customers.
System Scan
Support for detecting vulnerabilities in the following products was added to Authenticated Scanning:
- Apache Zeppelin
- Snappy Java
Support for detecting vulnerabilities in the following products was added to Authenticated Scanning for Windows:
- FPGA Support Package for the Intel oneAPI DPC++/C++ Compiler
- Intel Advisor
- Intel Connectivity Performance Suite
- Intel Distribution for GDB
- Intel DPC++ Compatibility Tool (DPCT)
- Intel Integrated Performance Primitives (IPP)
- Intel oneAPI Data Analytics Library (oneDAL)
- Intel oneAPI Deep Neural Network Library (oneDNN)
- Intel oneAPI DPC++ Library (oneDPL)
- Intel oneAPI Math Kernel Library (oneMKL)
- Intel oneAPI Threading Building Blocks (oneTBB)
- NetSupport Manager
- QEMU
- Schneider Electric Software Update
Elements Foundations
Integrations
WithSecure Elements API
New remote operation (Send Full Status)
We have added API support for the sendFullStatus remote operation, allowing administrators to request a full status report from devices. This operation is available for both computer and mobile devices and requires no additional parameters. After the operation is sent, the target device(s) will asynchronously send their status to the Elements Cloud.
Read more from the api specification page under POST /devices/v1/operations endpoint.
New API Endpoint: Get Incident Updates
We have added a new endpoint to the Elements API that provides programmatic access to incident update history.
Endpoint Details
GET /incidents/v1/updates
Description
This endpoint retrieves the complete history of changes made to a specific incident (Broad Context Detection). Each update represents a modification to the incident over its lifecycle, including status changes, detection additions, comments, and other modifications.
Key Capabilities
Update Types Tracked
- Status changes (patch)
- Detection additions, removals, and modifications
- User comments
- Response actions
- Incident merges
- Risk level adjustments
- Category changes
- Threat investigation and validation results
State Tracking
Each update includes stateBefore and stateAfter objects, allowing you to see exactly what changed. This includes status, resolution, risk level, and categories.
Origin Information
Updates include source information indicating whether the change was made by:
- A user (with display name)
- An automated engine
- A response action
Pagination Support
Results can be paginated using anchor-based navigation, with a configurable limit of 1-100 updates per request (default 50).
Filtering
Filter updates by type to retrieve only relevant changes (e.g., only comments or only status changes).
Customer Benefits
- Complete Audit Trail: Access the full history of incident modifications for compliance and reporting purposes.
- Accountability: Identify who made specific changes to incidents through origin tracking.
- Integration Support: Build automated workflows that respond to specific types of incident updates.
- Change Analysis: Compare before and after states to understand the evolution of an incident.
- Efficient Data Retrieval: Use type filtering to retrieve only relevant updates, reducing unnecessary data transfer.
- Scalability: Pagination support allows handling incidents with extensive update histories.
Read more from the Elements API specification page under "Get Incident Updates".
New "restart" remote operations
We have added two new remote operations to the Elements API device operations endpoint that enable programmatic system and agent restarts.
Operations Overview
The new operations "restartSystem" and "restartProduct" are available via the POST /devices/v1/operations endpoint.
New Operations
restartProduct
Restarts the WithSecure agent software on a device without restarting the entire system.
restartSystem
Restarts the entire device (full system reboot).
Batch Capability
Both operations support batch execution on up to 5 devices per request.
Benefits
- Agent Troubleshooting: Restart the WithSecure agent without disrupting the user's work by avoiding a full system reboot.
- Maintenance Automation: Integrate system restarts into automated maintenance workflows following software updates or configuration changes.
- User Communication: Provide advance notice to users with custom messages before system restarts, improving user experience.
- Efficient Remediation: Quickly restart multiple devices as part of incident response or troubleshooting procedures.
- Granular Control: Choose between agent-only or full system restarts based on the specific troubleshooting or maintenance requirement.
- Operation Tracking: Track restart operations using returned operation IDs to verify execution on remote hosts.
Read more from the Elements API specification under "Trigger remote operations on devices".
New response actions to enable new workflows
We've added new response action endpoints under
POST /response-actions/v1/execute/<name>
to expand remote execution capabilities for both device and identity management.
This allows you to automate new workflows that involve acting on the target devices and identities.
This release increases the number of API supported response actions from 8 to 32.
Device response actions
The following device response actions are available:
- Create full memory dump - Uploads a full memory dump from the device
- Delete registry key or value - Deletes a specified Windows registry key or value
- Delete scheduled task - Deletes a specified Windows scheduled task
- Delete Windows service - Deletes a specified Windows service
- Delete WMI persistence objects - Deletes Windows Management Instrumentation (WMI) persistence objects
- Enumerate running processes - Enumerates running processes on the device
- Enumerate WMI persistence mechanisms - Enumerates WMI persistence mechanisms, including event consumers, filters, and bindings
- List file system structure - Lists the file system structure based on path matching patterns
- List registry keys and values - Lists Windows registry keys and values based on path matching patterns
- List scheduled tasks - Lists all Windows scheduled tasks on the device
- Retrieve amcache files - Retrieves the application compatibility cache file from the device
- Retrieve antivirus logs - Retrieves antivirus software log files for security analysis
- Retrieve browser artifacts - Retrieves the browser history from the device
- Retrieve event log tracing files - Retrieves .etl event log tracing files with records of system activities
- Retrieve files from device - Retrieves files from the device based on path matching patterns
- Retrieve jump list files - Retrieves jump lists stored in the AutomaticDestinations and CustomDestinations subfolders
- Retrieve master boot record - Retrieves the master boot record (MBR) from a specified drive
- Retrieve master file table - Retrieves the master file table (MFT) from a specified drive
- Retrieve network connections - Retrieves network connections, routing tables, interface statistics, and related process information
- Retrieve prefetch files - Retrieves Windows prefetch files with evidence of program execution
- Retrieve process memory dump - Retrieves a memory dump of a specific process
- Retrieve RDP cache files - Retrieves remote desktop protocol (RDP) bitmap cache files
- Retrieve recently accessed files - Retrieves information about recently accessed files and folders from user activity artefacts
- Retrieve registry hive files - Retrieves Windows registry hive files
- Retrieve SRUM database - Retrieves the system resource usage monitor (SRUM) database
- Retrieve Windows event log entries - Retrieves Windows event log entries based on specified filters
- Retrieve Windows event log files - Retrieves Windows event log files
- Terminate process - Terminates processes matching the specified patterns
- Terminate thread - Terminates a thread
Identity response actions
The following identity response actions are available for Microsoft Entra:
- Block user access in Microsoft Entra - Blocks access for a user to all resources inside the Microsoft Entra ecosystem
- End Microsoft Entra session - Ends the Microsoft Entra session of a user
- Reset Microsoft Entra password - Resets the Microsoft Entra password of a user
Response action results and attachments
Response actions are processed asynchronously: once triggered, you can monitor their progress.A new endpoint is available for retrieving the actual results of response actions that return data (for example, memory dumps or other files):
GET /response-actions/v1/responses/tasks
By using this endpoint, you can download any files or attachments produced by completed response actions. To determine when your action has finished, first poll the state via GET /response-actions/v1/responses. When the action is marked as finished, your attachments are ready for download from the tasks endpoint.
Start building
Full API documentation is available at Elements API Reference | WithSecure™ Connect
Other items of interest
Threat Advisory October: Docker Compose Path Traversal Vulnerability (CVE-2025-62725)
Technical Summary
- A critical vulnerability in Docker Compose's handling of OCI-based artifacts allows attackers to perform path traversal and write arbitrary files to the host system. This flaw stems from improper validation of layer annotations in YAML files, which are widely used in CI/CD pipelines and development environments.
- Attackers can exploit this flaw by tricking users into referencing a malicious remote artifact. This enables them to escape the Compose cache directory and write files anywhere the Compose process has permissions—potentially leading to full host compromise, data tampering, or privilege escalation.
Share your ideas with us
Our purpose is to co-secure the world with you – now as WithSecure™. To co-create the best possible cyber security products and services, we warmly recommend you share your ideas via the Ideas section of the WithSecure Community, now accessible directly from WithSecure™ Elements Security Center.
Further information
Changelogs and Release Notes for all parts of WithSecure™ Elements can be found at the Help Center