Editor’s Highlights
Outbreak Control – This new feature brings a powerful capability to dynamically and temporarily increase security when an EDR detection has been made on devices. You can find out more in the Elements Security Center section below.
Elements Security Center
New Features
Outbreak control: Outbreak control is an extension for profile assignment rules. When change tracking is enabled, you can create a rule that automatically reacts to open EDR detections and assigns a hardened profile and custom labels to the affected endpoint. Once the detection is closed it will automatically change the profile and labels back based on your other rules

Security Posture (piloting release) Security Posture analyzes your devices and profiles to find common weaknesses that lead to devices being compromised or confidential data being leaked. You can click on the items to see further explanations and instructions.

Slightly later in the month, we also added two more new recommendations: "Over 10% of workstations have been last logged in by an admin user" and "System integrity protection is disabled”.

Improvements
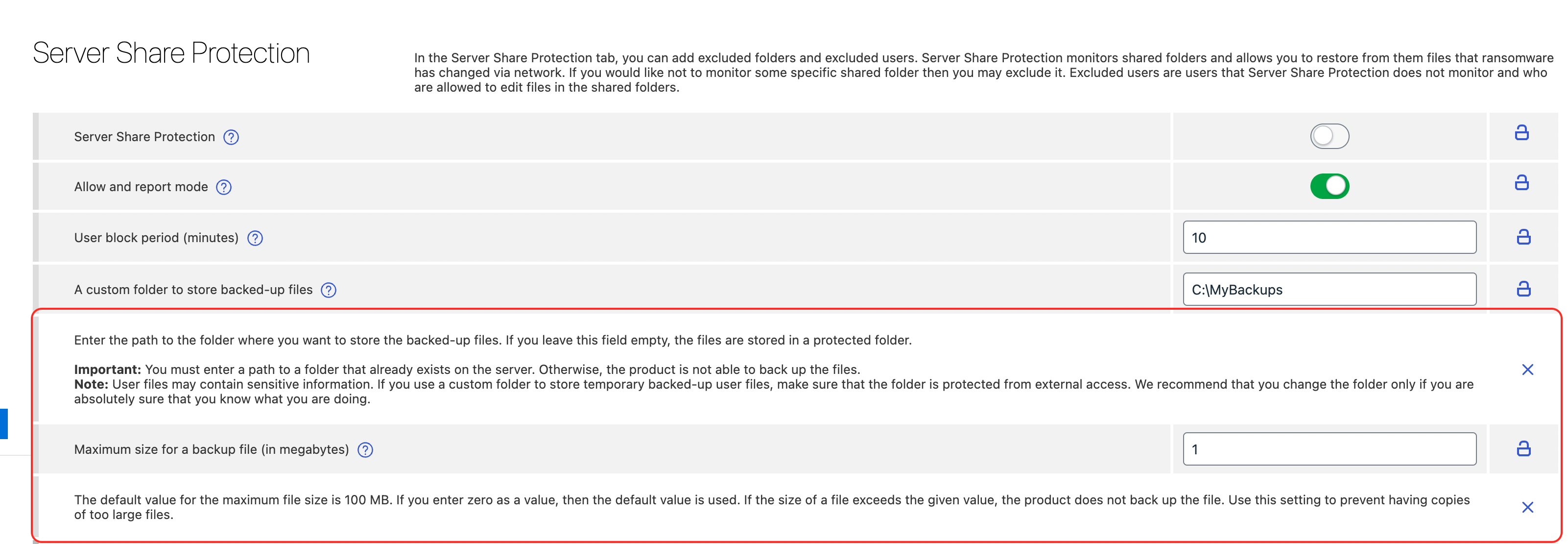
Server Share Protection: We have added the possibility to set a folder for backups and to set a maximum backup file size.
Network Location Settings. It is now possible to override settings even if they are locked in the profile. The red notification is not needed anymore.

Device View. Monthly scanning counters have been added to the devices view. You can see how many files were scanned and how many issues were found during the month. These counters can be used to make queries.

My Reports. Customers can now provide feedback about the new My Reports view. We are gathering feedback to further improve and make this new functionality more useful.
Audit Logging. Changes and operations done in the profile assignment rules page are now visible in the Audit Log.
Device Details. We have improved the readability of local and admin exclusions in the device details by rendering the path as a list. If any of the exclusions are considered dangerous they are now highlighted in the list.
Security Events. Events can now be filtered by the device labels. It is important to note that any changes to the labels assigned to the device are to be visible only in the events happening after the label change was made. No changes to historical data is ever made.

Similar to what has already been available in the Devices view now also Security Events view supports Saved Views. With the initial release a set of predefined system views is shipped together with an option to create custom user views.

Multiple Proxy Support (Windows). We have added multiple proxy support to windows proxy settings. This will be available with clients 23.4+

Show discovered shared folders. To increase visibility of folders shared from a device, for example useful with Server Share Protection, we now show ”shared folders” in the Devices view and the Devices details pages.


Advisory dashboard. The pie-charts are now displayed with legends to aid readability and understanding.

Elements Endpoint Protection
WithSecure Elements Mobile Protection app for iOS released
An update to the WithSecure Elements Mobile Protection app for iOS (23.0.10134) has been released. It includes the following new features and improvements:
- The app is now more reliable when running in the background.
- The About view in the app and the WithSecure Elements Endpoint Protection portal now show if a device is enrolled in an MDM.
- The app no longer has a blurry screen in the multitasking apps manager.
- When terminated, the app now shows a notification and informs the WithSecure Elements Endpoint Protection portal.
- The app and the WithSecure Elements Endpoint Protection portal now support remote operations.
- The app version format is now compliant with the other WithSecure products.
Elements Collaboration Protection
New features and improvements:
Hidden inbox rules. The hidden inbox rules expound a serious threat in Microsoft Exchange Online. The threat actors could abuse the inbox rules as one of the instruments of the targeted attacks, e.g., to spread malware among user contacts, attempt to steal or destroy information. The hidden rules make these attacks almost impossible to detect with out of the box tools. Elements Collaboration Protection introduces the new feature: ‘Suspicious hidden inbox rules’. That feature allows the detection of suspicious rules, and notifies the user and security administrator about them, so they could respond to the potential attack vector.
SharePoint URL. A site URL info was added for SharePoint assets in cloud services view as extra information to differentiate sites.
Visual improvements. The assets and status tags were updated across the Collaboration protection portal to improve visibility and unify user experience.
Elements Vulnerability Management
Elements Vulnerability Management Portal
CVSS v3.1
Elements Vulnerability Management has introduced a new scoring system to align with industry standards and vulnerability scoring in Elements EPP. Vulnerability scoring changes from CVSS v2 to v3.1. The 4-level vulnerability severity scale changes to 5-level.
The transition to CVSSv3 scoring system has a significant impact on the vulnerability evaluation, as it provides a more comprehensive and accurate way of assessing the severity of vulnerabilities. The new 5-level vulnerability severity scale is a consequence of transitioning to CVSSv3 and provides better visibility to the most critical vulnerabilities, out of high-severity vulnerabilities.

The following link provides more detailed information regarding the CVSSv3: https://www.first.org/cvss/v3.1/user-guide.
The transition to CVSSv3 scoring for organizations' vulnerability data in the portal may take some time. The primary indicator is the scan schedule and the frequency of re-evaluation of vulnerabilities for specific scan targets. For traditional, network-based vulnerability scanning, we recommend that you rerun all scans to obtain vulnerability data and severity counters that are calculated according to the new scoring system.
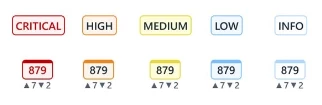
The vulnerability severity counters will start providing 5 different severity levels, including Critical, High, Medium, Low, and Info. Note that from now on, the red color is reserved for Critical vulnerabilities, while High vulnerabilities are presented in orange.

The changes in vulnerability scoring do not only apply to the most critical vulnerabilities with a CVSSv3 Base Score of 9.0 or higher. As part of this transition, you may notice that the same vulnerability scored in both v2 and v3 can have a different result in new severity scores. Our research indicates that the average base score increases from 6.5 in CVSSv2 to 7.4 in CVSSv3.
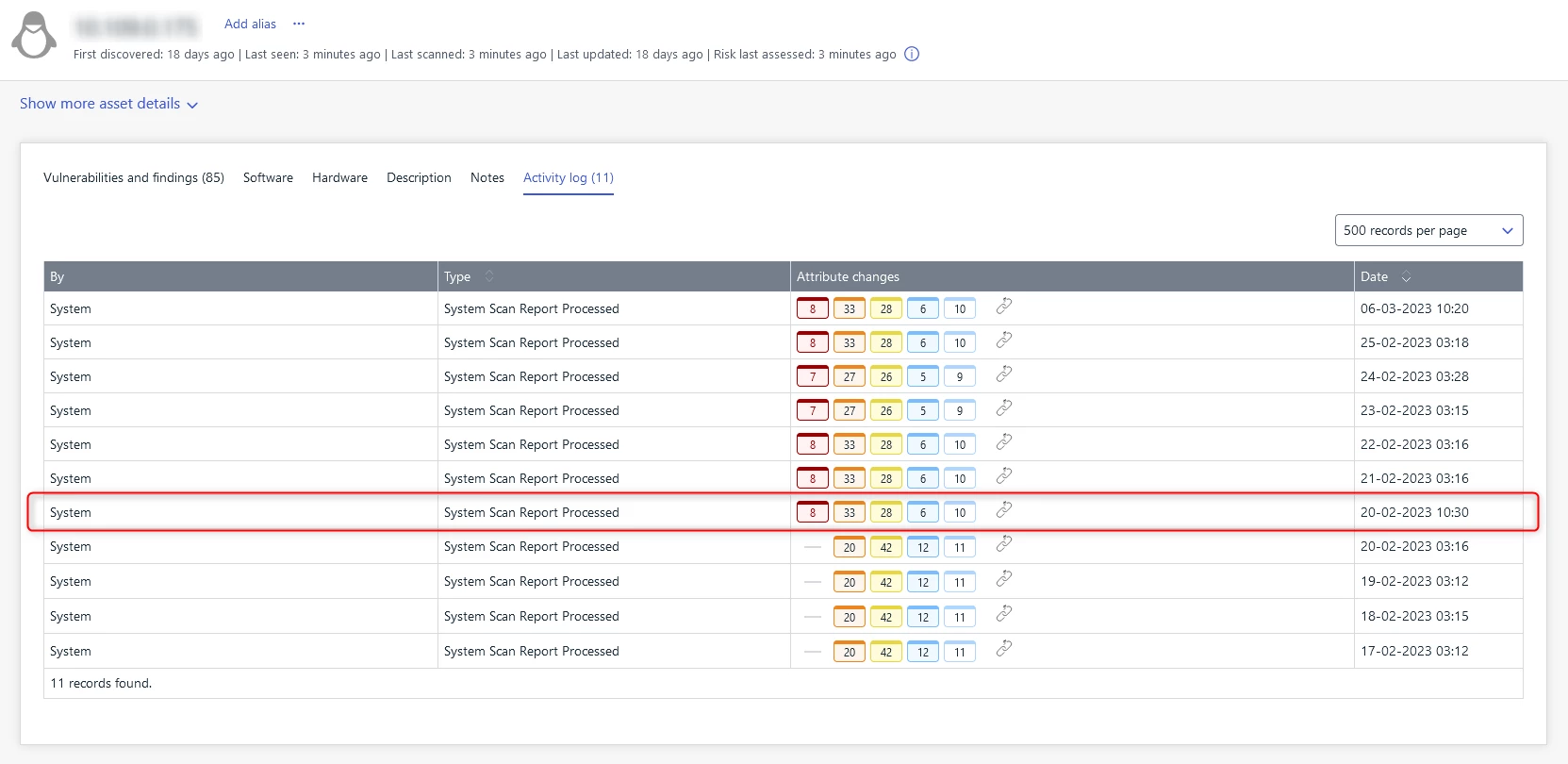
To help customers identify vulnerabilities with a changed score, the Elements VM portal introduces an informative icon (with help text) that is next to the vulnerability title. As seen in the example screenshot, the icon provides information that the severity scoring has changed, which may result in the vulnerability being re-categorized from Medium to High severity, for example.

For reference or to compare the current vulnerability score with the past, go to the Vulnerability Details page that shows both the CVSSv3/v2 vector and base score.

A similar scenario can occur in the assets' Activity log or in the historical overview of individual System/Web scan reports, because vulnerabilities that are evaluated after March 8 may have been assigned new severity scores aligned with CVSSv3.

To expedite the migration process, we recommend that you perform manual re-scans for all targets. This can help to quickly overcome any inconveniences and challenges associated with comparing previous scan cycle results with the current security posture.
In addition, the email notifications have been updated to comply with the new CVSSv3 standard.

Elements Vulnerability Management System Scan
During March, we added the capability to detect vulnerabilities in multiple products to the System Scan's authenticated scan on Windows:
- Sophos Connect Client
- McAfee Active Response
- HP Support Solution Framework
- IrfanView
- Watchdog Anti-Virus
- Intel Manageability Commander
- Amazon AWS WorkSpaces client
- Cisco Secure Endpoint (formerly Advanced Malware Protection (AMP) for Endpoints)
- NSClient++
- GIMP
- Intel Trace Analyzer and Collector
- Git LFS
- HP Version Control Agent
- HP Insight Management Agents
- IBM Spectrum Protect (aka Tivoli Storage Manager) Client
- OpenVPN Connect
- OpenVPN Community edition
Integrations
Elements API
Listing EDR detections and isolating computer from network
Listing detections of EDR incident - This allows the acquisition of details of an EDR incident in order to perform triage from a third party platform . The client can use the incident ID received from security events to query the list of detections from EDR detection engine.
Isolating computer from network and releasing from isolation – The client can send acommand that isolates workstation or server at risk. Support for other remote operations will be extended in the future.
Reading list of remote operations – The client can check status of remote operation for
particular computer.
Triggering remote operations is only allowed for clients with Read/Write permissions.Getting Started guide contains information how to add credentials with required permissions.
Other items of interest
WithSecure Elements Quarterly Launch
Once a quarter, we take a more detailed look at some of the things we have released. You can find the things we are most excited about at
https://www.withsecure.com/en/solutions/software-and-services/elements/withsecure-elements-quarterly
In case you missed it
Compromised 3CX desktop app in a supply chain attack
Trojanized versions of the 3CX desktop app (VOIP) are being used in an ongoing supply chain attack.
Read more from here what WithSecure can do to help customers.
Share your ideas with us
Our purpose is to co-secure the world with you – now as WithSecure™. To co-create the best possible cyber security products and services, we warmly recommend you share your ideas via our Ideas Portal, now accessible directly from WithSecure™ Elements Security Center.

Further information
Changelogs and Release Notes for all parts of WithSecure™ Elements can be found at the Help Center