Application control exclusion rules explained This article applies to the following F-Secure products: Computer Protection, PSB portal, Policy Manager.
Application control is a premium feature that strengthens your protection for the installation and launch of applications, installers, and scripts. Predefined rules designed by F-Secure security experts block many of the common attack vectors of existing malware. In Application control, you can also add your own rules by selecting Add exclusion.
Before deploying a new block rule, consider setting the rule action to Allow and monitor. All the application events matching the rule are reported in the Applications tab in the device details view.
When creating a new rule, note that the order of the rule is important. For example, you may create a specific allow rule before a generic block rule to allow a specific application to run. You can use the arrows in the profile editor to change the rules order.
Here we outline ways in which Application control offers prevention from attack vectors, such as common zero days and targeted attacks. The 3 main scenarios are:
- Prevent Microsoft Office exploit vulnerabilities;
- Block unwanted applications; and
- Restrict vulnerable applications by version.
Prevent Microsoft Office exploit vulnerabilities
With malware exploits using MS Office vulnerabilities on the rise, it is becoming more common that malware of this type is being spread via documents arriving into a company network. Once the malware gets in, it can set itself up on the victim host and may also launch a new process, such as a PowerShell scripting engine.
As an admin, you can therefore increase the security of your organization and block Microsoft Office programs from starting other apps. This type of restriction does not affect a normal user's work, as Microsoft Office applications do not usually start other apps.
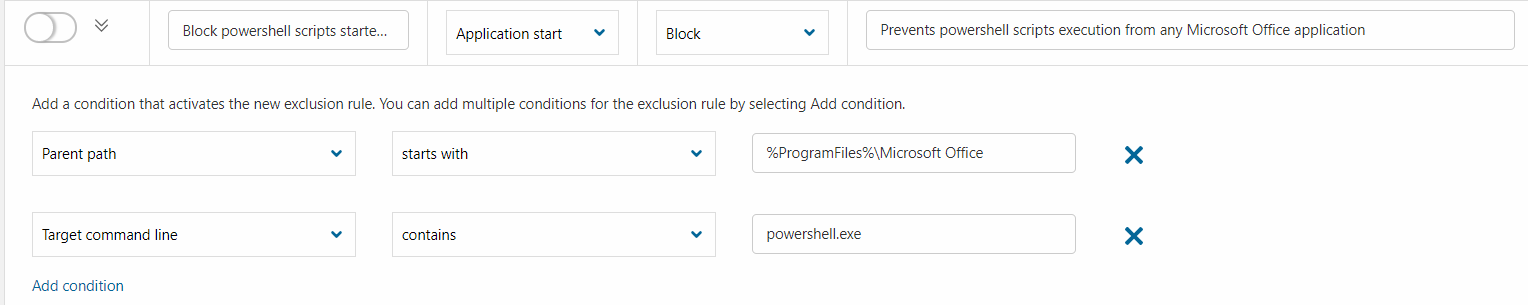
To explain the rule further:
- The Parent path parameter refers to the application launcher, for example,
winword.exe.
Note: The exclusion rule expects that Microsoft Office is installed under the default location and uses the %Program files% environment variable. Application control supports system and user environment variables.
-
The
Target command line parameter restricts the rule further by blocking only the powershell.exe processes.
Note: To block any application from starting in MS Office, remove the second parameter.
As powershell.exe is commonly used to configure workstation settings - if needed, you can then create an additional rule that disables the powershell.exe restriction, but allows only your own personal scripts. In the screenshot, we assume that your management scripts are stored under c:\myscripts.
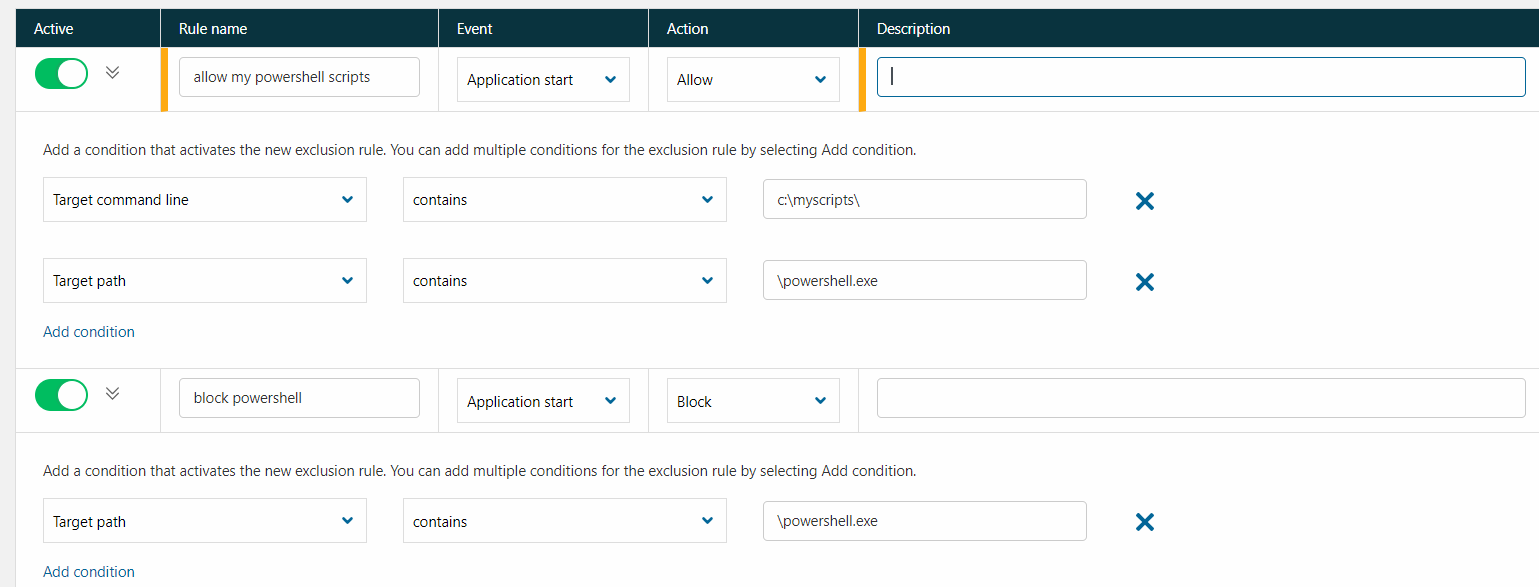
The exclusion rule explicitly allows powershell.exe, if its condition is c:\myscripts\.
For example: powershell C:\myscripts\login.ps1
Note: The exclusion rule uses the "contains" condition to match paths, such as:
c:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
This condition may accidentally match the "c:\powershell.exe\myprogram.exe" path.
An alternative option is to specify the exact match with the "equal to value" as in:
"%SystemRoot%\WindowsPowerShell\v1.0\powershell.exe", or use the "ends with" condition.
Block unwanted applications
Application control can also help with blocking unwanted applications; for example, games. The following example shows how to block the installation of Steam games.
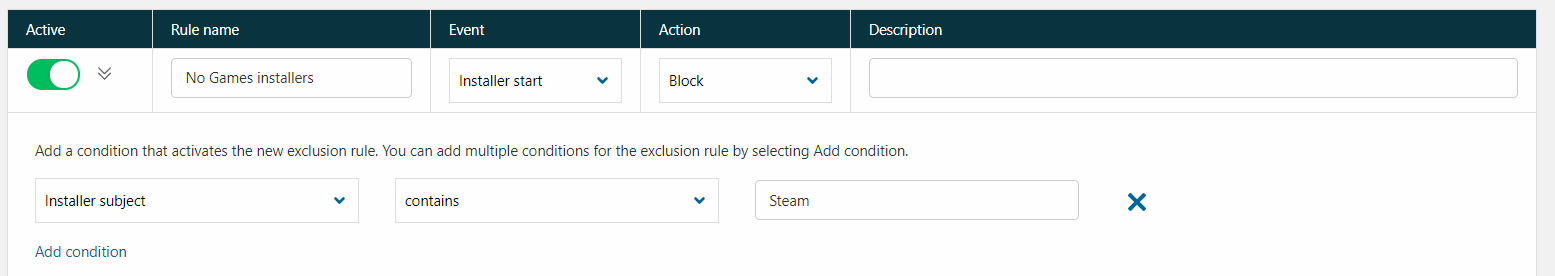
This rule is specified for MSI installers and blocks by installer subject, which is found in the Properties file:
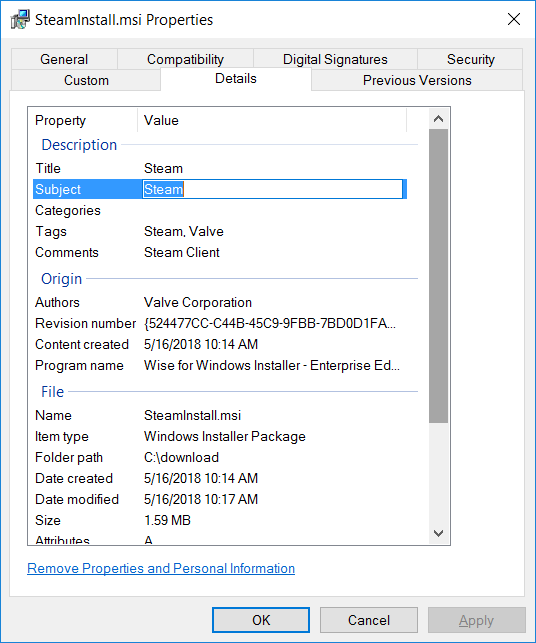
Application control allows you to specify rules for different meta properties of an application. The following example demonstrates blocking Spotify by copyright text:
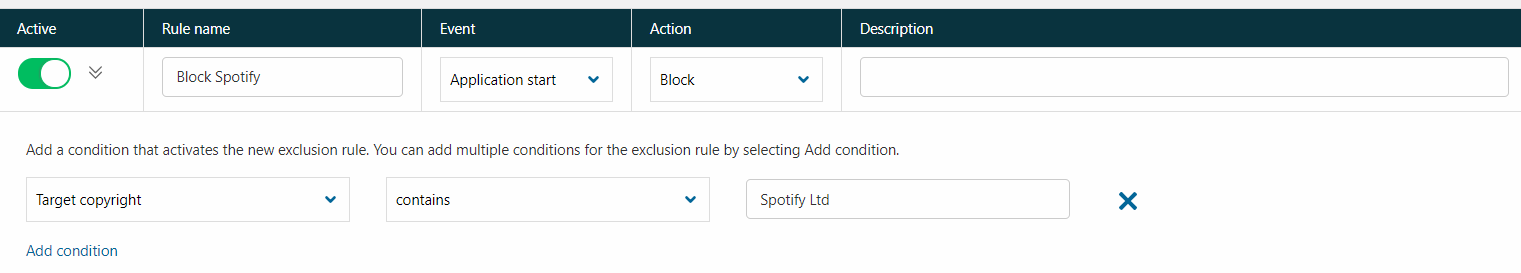
This rule blocks Spotify from starting regardless of where the file is installed. These properties are visible in the file details:
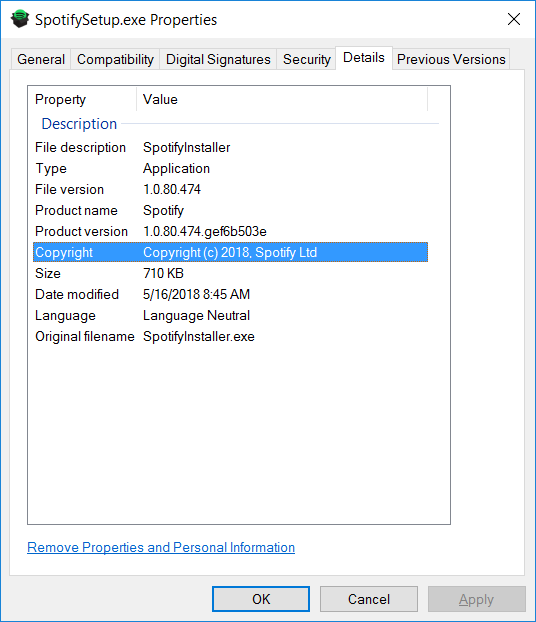
Restrict vulnerable applications by version
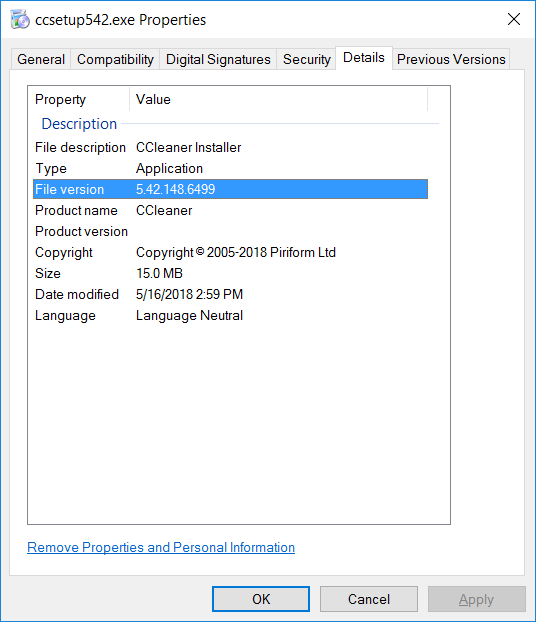
Application control is useful for restricting vulnerable applications from running, for example, to block an unpatched version. As an example, CCleaner has fixed a critical vulnerability in the latest version 5.42.148.6499 and any older versions can be blocked.
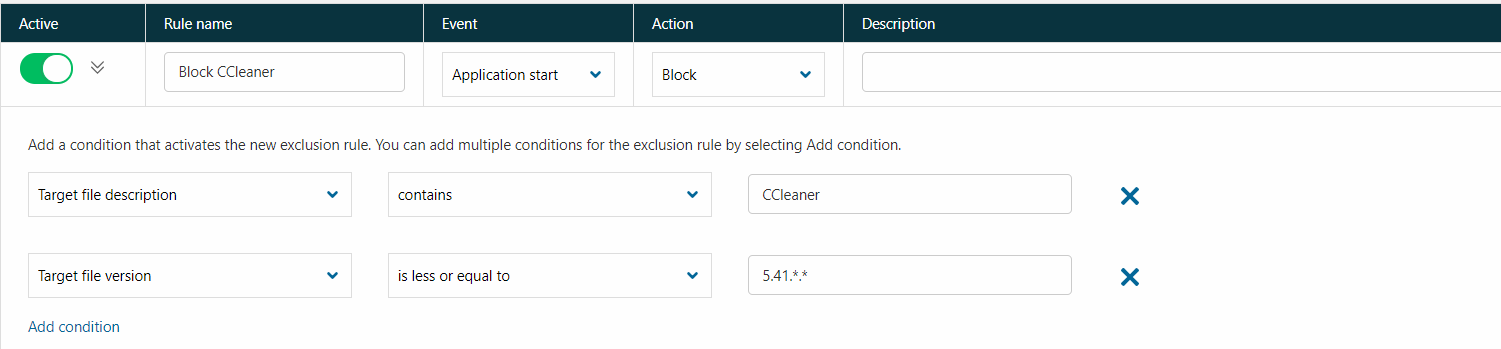
The condition for the target file version 'is less or equal to 5.41.*.*' The asterisk field indicates that only major and minor fields are used in comparison. As "CCleaner" is in the Target file description, the program is blocked regardless of the file name or its location.
Tip: To find the file version, check the Properties file.